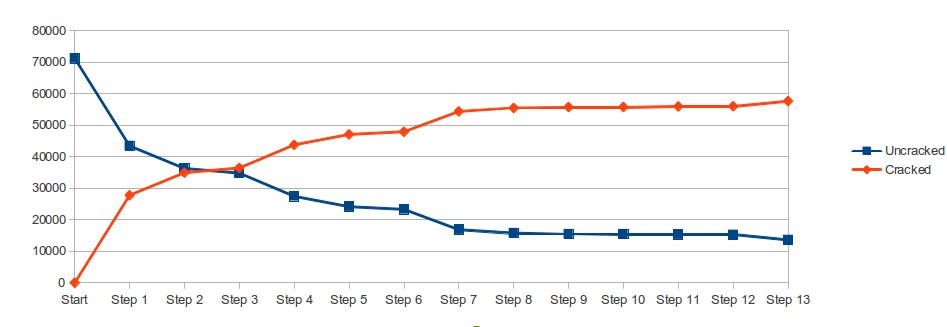
The simple fact is, as you guess the easier passwords you are ending up with the more difficult passwords. At some stage in the process you will cross the point where these types of steps are no longer viable or effective, and it is at that stage when you need to begin trying to come up your own ways to make your cracking more effective (password profiling, new mangling techniques or rules, etc). That is when it becomes not about your CPU/GPU cycles and dictionary, but about you.