FFGBEACH = HEAD+DESK
Let me start by saying I was not sure about writing this particular
article but after some serious thought I figured not doing so would be
doing more harm then doing it. This article is a documentation of a
tragedy of errors that shows how bad things can be, the lies a company
can tell and just general stupidity (I make no apologies for using that
term by the way). Before we start, all screenshots I show come from the
last 2 days. This is important as you will see...
I make a point of trying to keep fairly up to date with password leaks
and dumps. so I saw these:
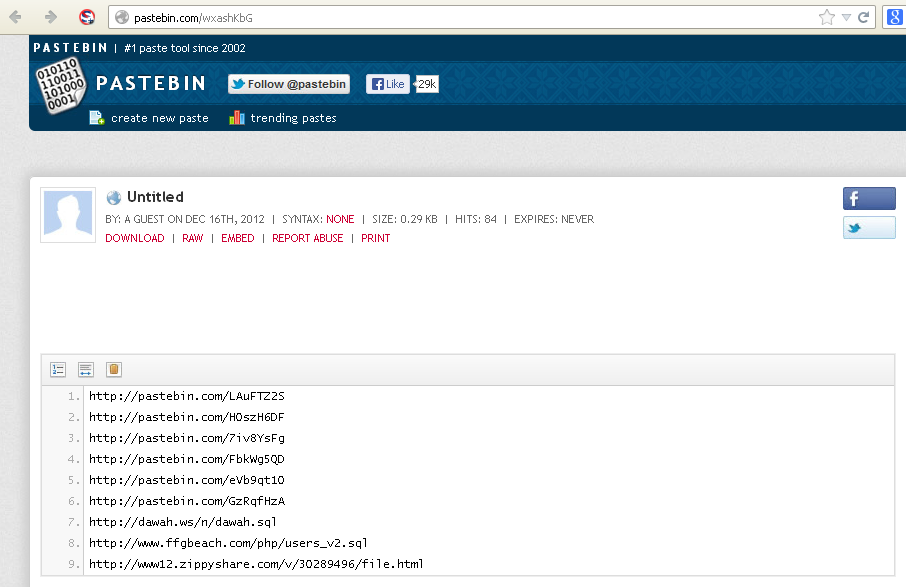
..and
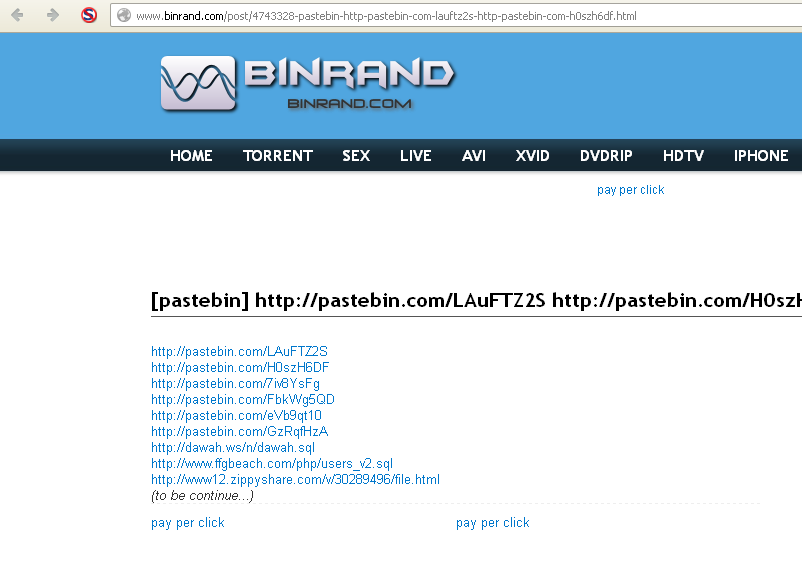
Now the pastebin link shows when it was posted - December 2012. So I
thought "no way is this still valid, this would be gone by now. I mean
I am 4 months late!". But I still went to go take a look optimist that
I am (silly, silly me). And I see this:

WTF! Directly after seeing this I am telling myself "No way is this
real, this is a fake dump! Still live after 4 months? Has to be fake.". So
I looked around I little. I went to the "php" folder in the url:
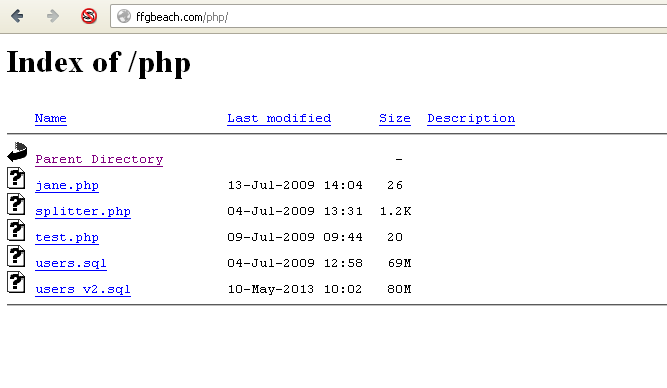
I went back to the root of the site:
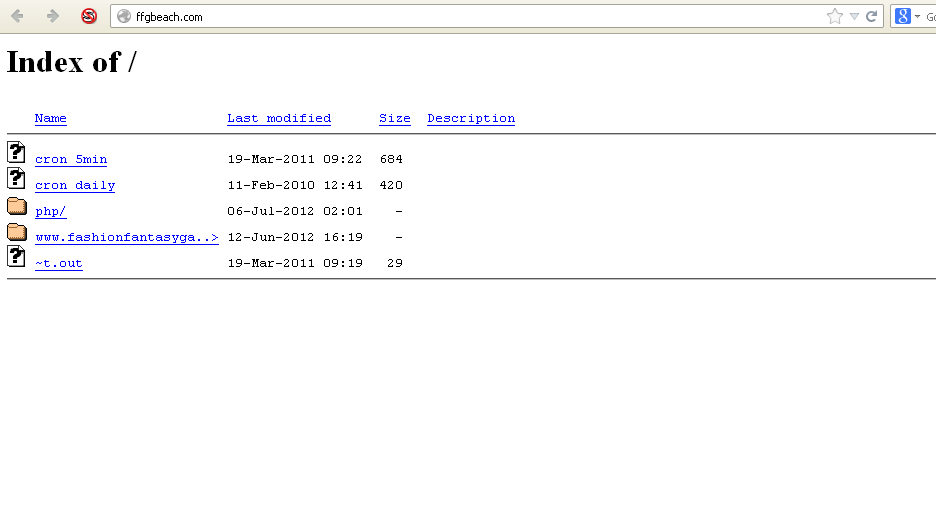
I went digging a bit and saw:
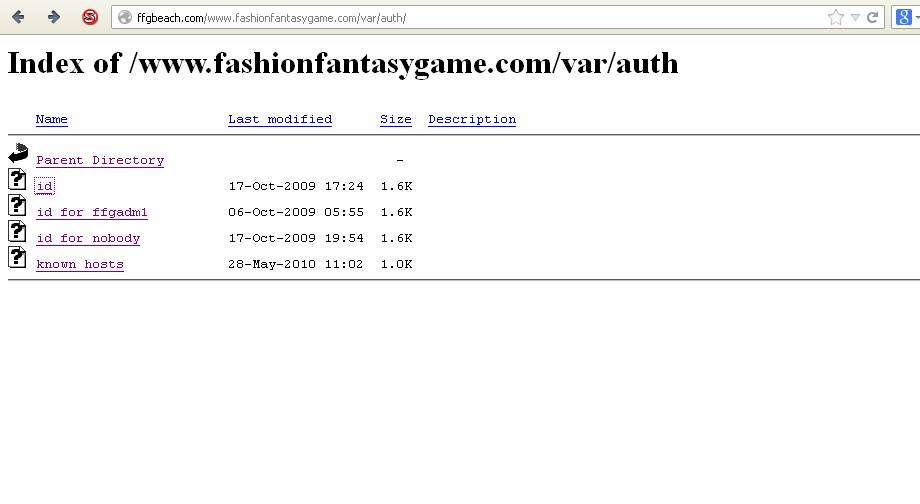
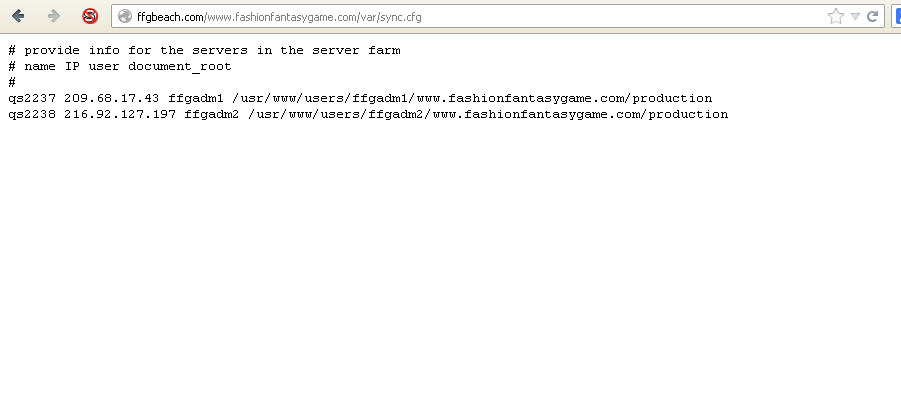
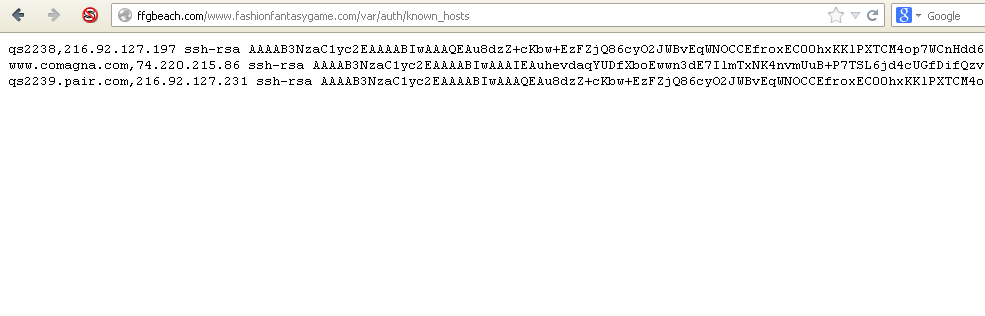
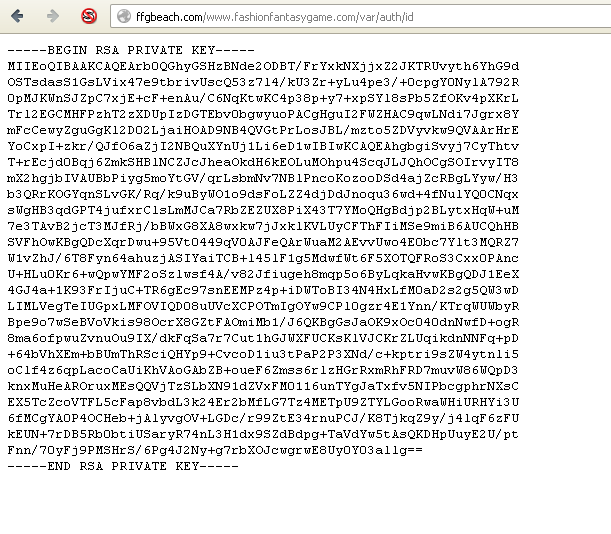
Once again.... WTF!! So a large part of me still thinks this fake, but
now I start thinking maybe (looking at the folder structure) someone
has compromised a site and has moved the juicy files onto a holding
site. So I dig a bit more:
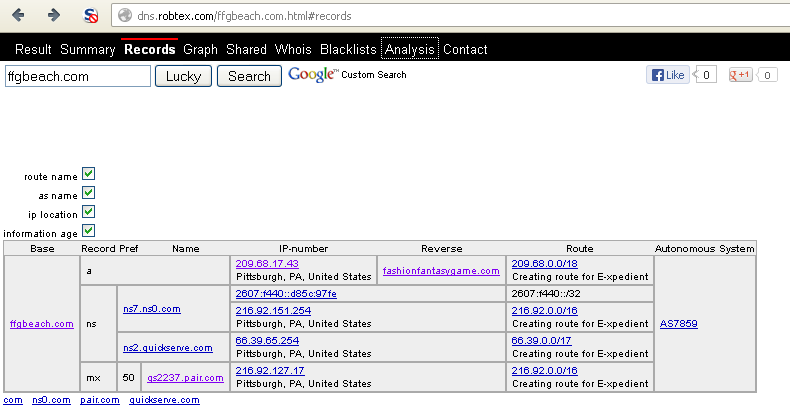
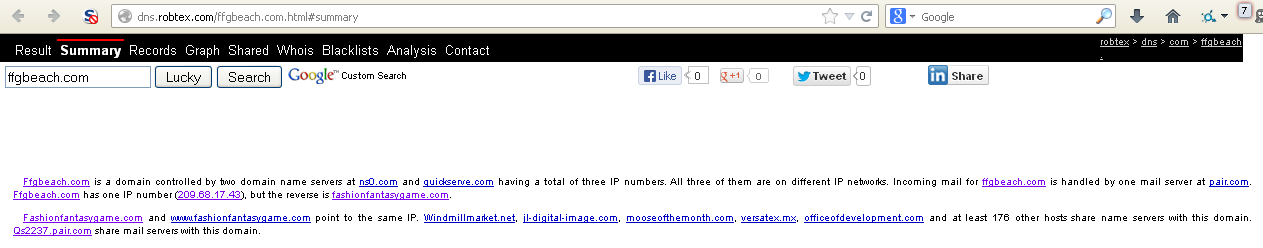
All together now.... W. T. F. !! So I was wrong.
"fashionfantasygame.com" is very much linked to "ffgbeach.com". So what
can I find about "fashionfantasygame.com"? Lets start with the
whois/dns information:
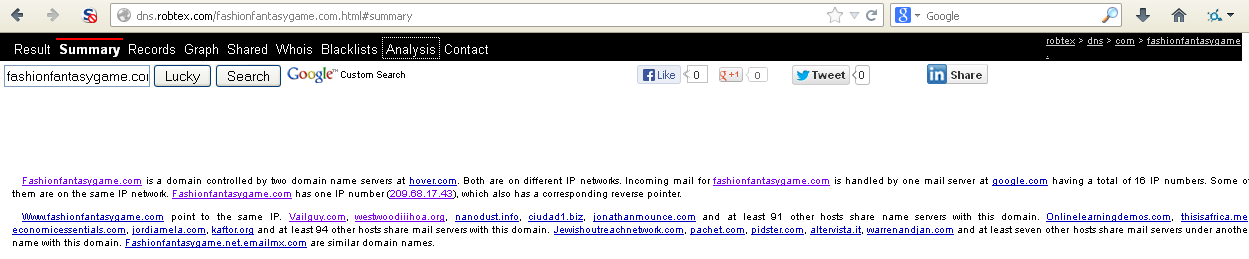
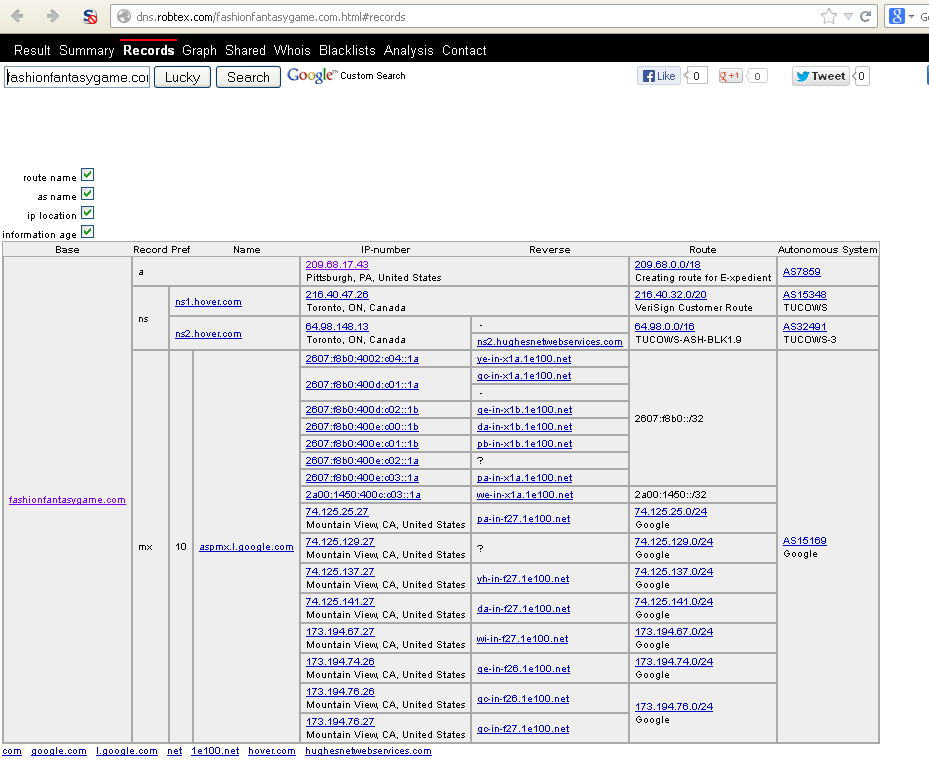
Interesting. Lets take a look at the site itself:
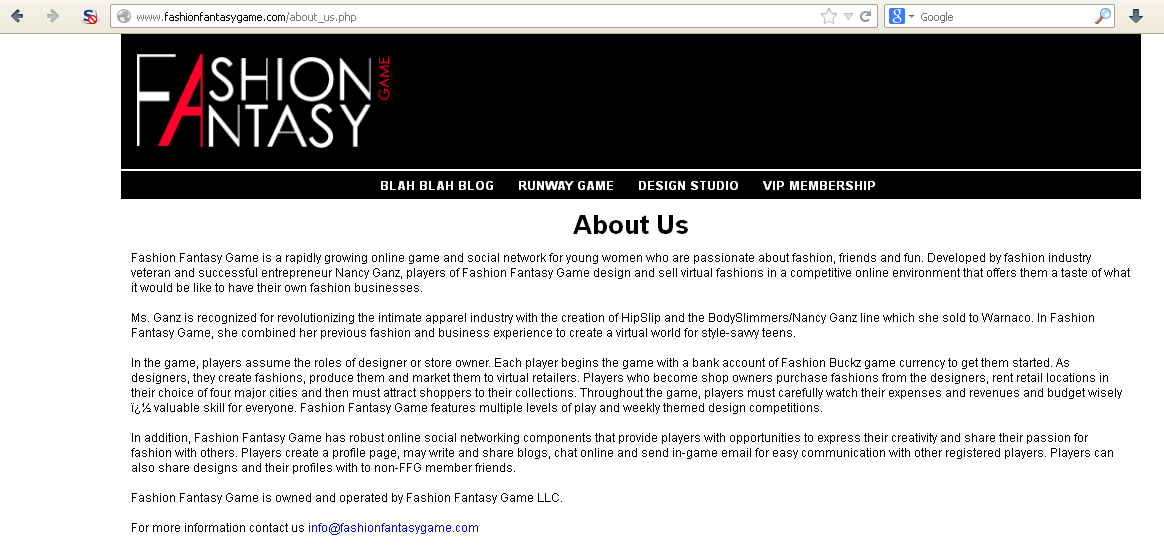
Read that very carefully. Look at the audience of this site. Now lets
look at the privacy policy:
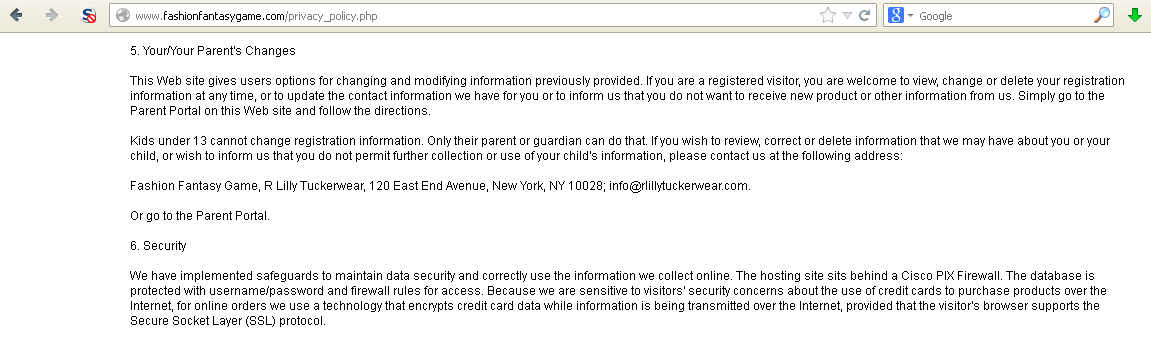
Again, read section 6 well. Credit card information? Allow me to
explain to "fashionfantasygame.com" a technical term that is
appropriate for describing your security measures and privacy policy,
it's "BULLSHIT". This is a site aimed at "young ladies" where paypal and
credit cards are used, where social interaction is encouraged, and this
is the level of care you think is appropriate!! That sql file has been
known to the less savoury parts of the internet for at least the last 4
months! But...take a deep breath... is it that bad? In a word, yes. The
hashes are unsalted md5 hashes. I took a quick run through them and I
cracked over 80%. To be exact at this exact moment as I write this (and
it is still running), I have 68245 hashes left. I have taken a quick
look through the passwords as well, there was very poor password
enforcement if anything - the password "123456" is used thousands of
times.
So lets recap:
We have a site ("fashionfantasygame.com") that deals with credit card
and paypal data, is aimed at young ladies and has had a sql dump of
their users publicly available to the internet for at least 4 months.
They did not salt the passwords. They did not enforce good password
standards. I cannot express the amount of "FAIL" this encompasses.
When I first started looking at this, I thought "someone else must have
written on this. someone else must have mentioned this." Well, I could
not find anything. If someone did, then good on you. But what about
now? My personal suggestions are:
1) All users of "fashionfantasygame.com" past and present - please,
please change your passwords. All of them. Check your online accounts
to make sure nothing has been tampered with.
2) All users of "fashionfantasygame.com" present -
quit "fashionfantasygame.com". Or if you feel like giving them
a chance in spite of their documented lack of care, then raise your
voice and get them to notify their users and change their
process and setup. Get them to take measurable steps to earn your trust
back.
3)
"fashionfantasygame.com" - ....I actually have no words. Or to be more
exact, I have no polite words for this level of due care with the data
of minors. Find someone who knows what the hell they are doing and let
them do what they need to.
Ok, I have had enough ranting, go and be good.














