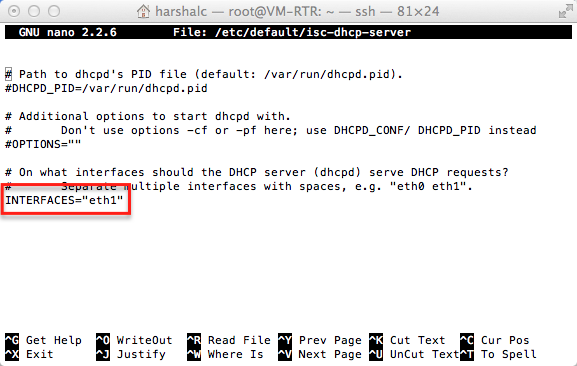
Ok so now whats next? We need to configure this machine to behave as a gateway. Lets do it.
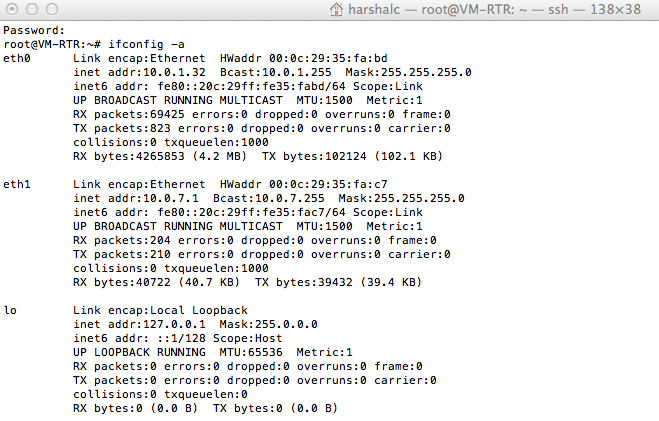
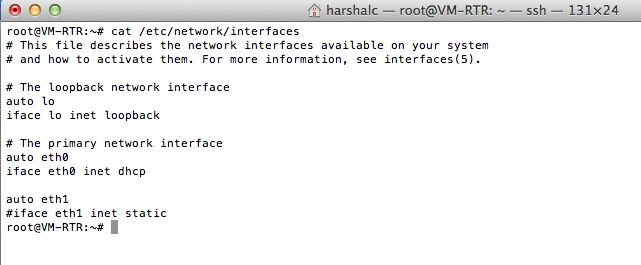
Is that how your ifconfig looks like? forget the ips but there should be two interfaces. My eth0 works as a WAN (External) and eth1 works as LAN (Internal).
Now lets take a quick look within esxi network configuration. From the vcenter
vcenter → select esxi host → right pane “configuration” → select “networking”
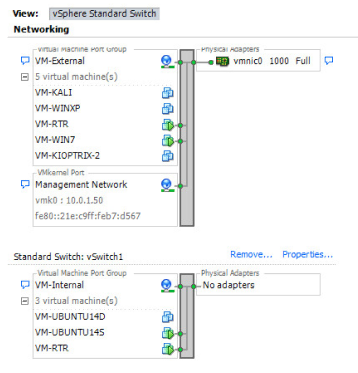
This should bring you to the following view. If you haven’t created something like “vSwithch1” then do it. Stay on this pane → top right select “add networking” → uncheck all adapters (no physical adapters should be connected)
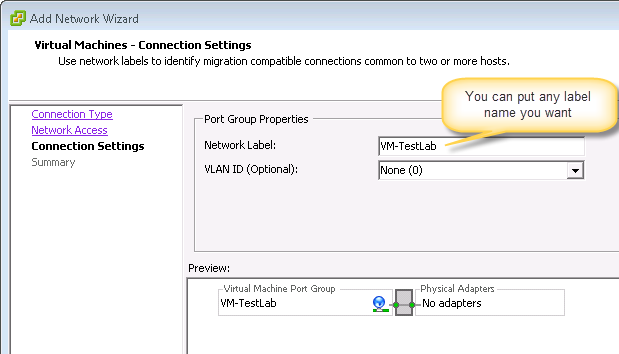
After you have configured your switch through the wizard, head to your vcenter → select esxi host → right pane “configuration” → select “networking” - it should look something like the figure below:
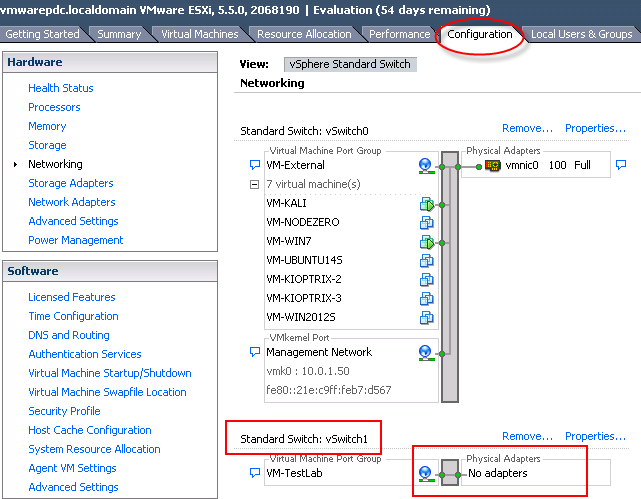
Now start assigning the new adapter VM-TestLab to the new machines that you have configured. In my case I named it VM-Internal. I created 2 VMs after this